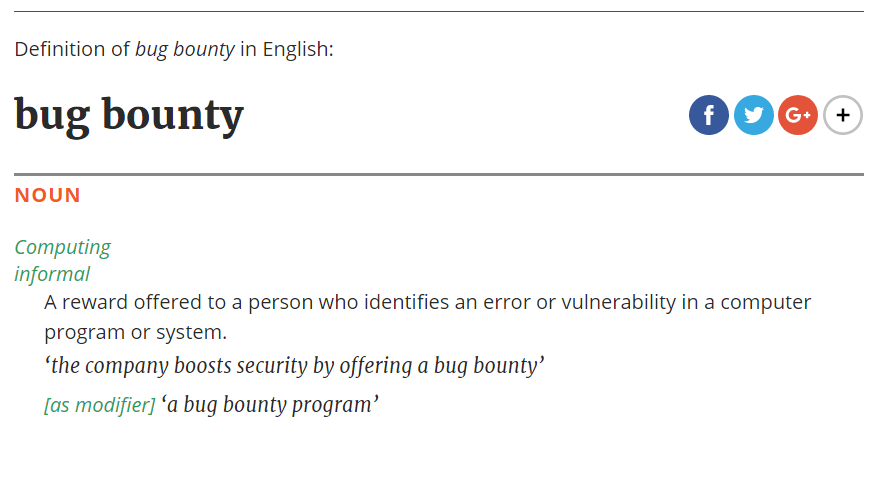
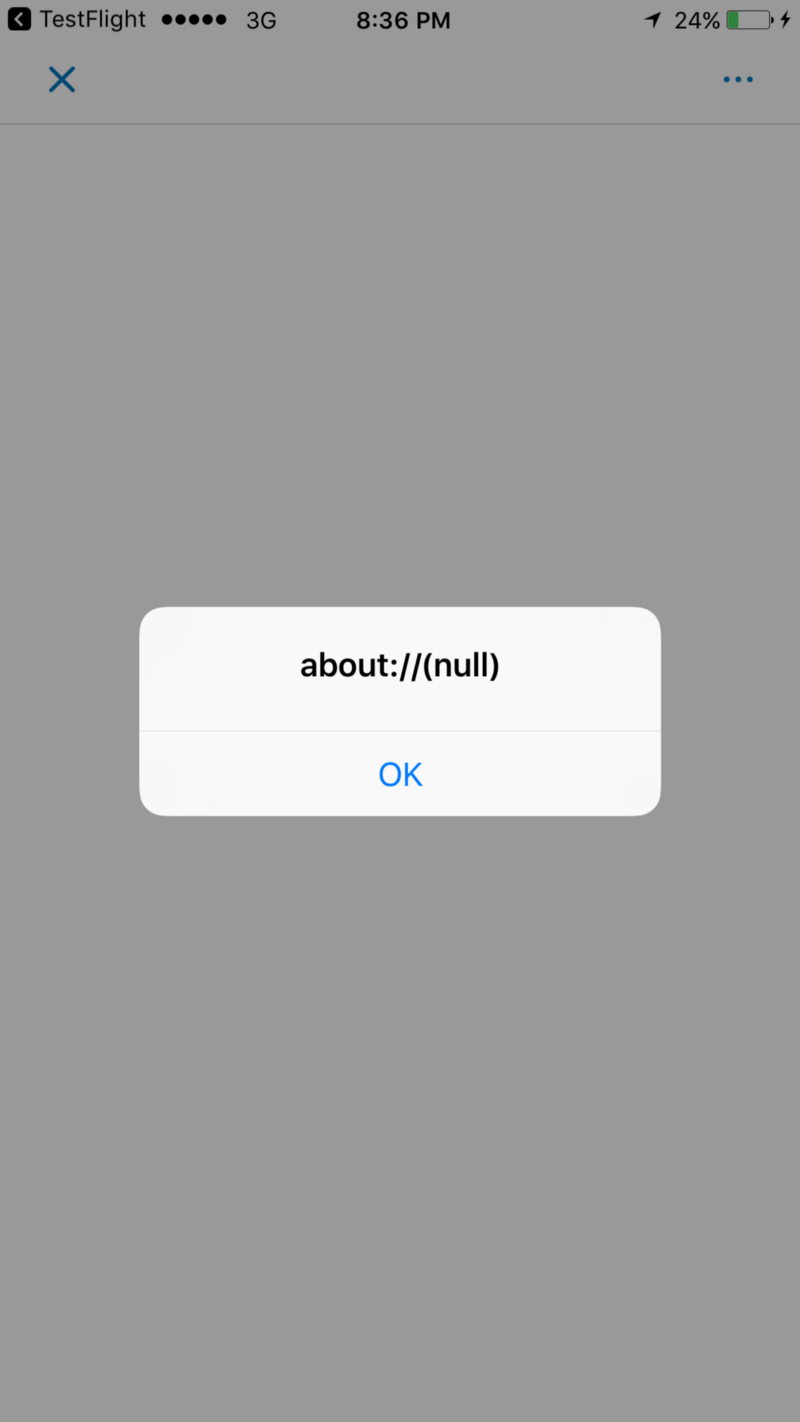
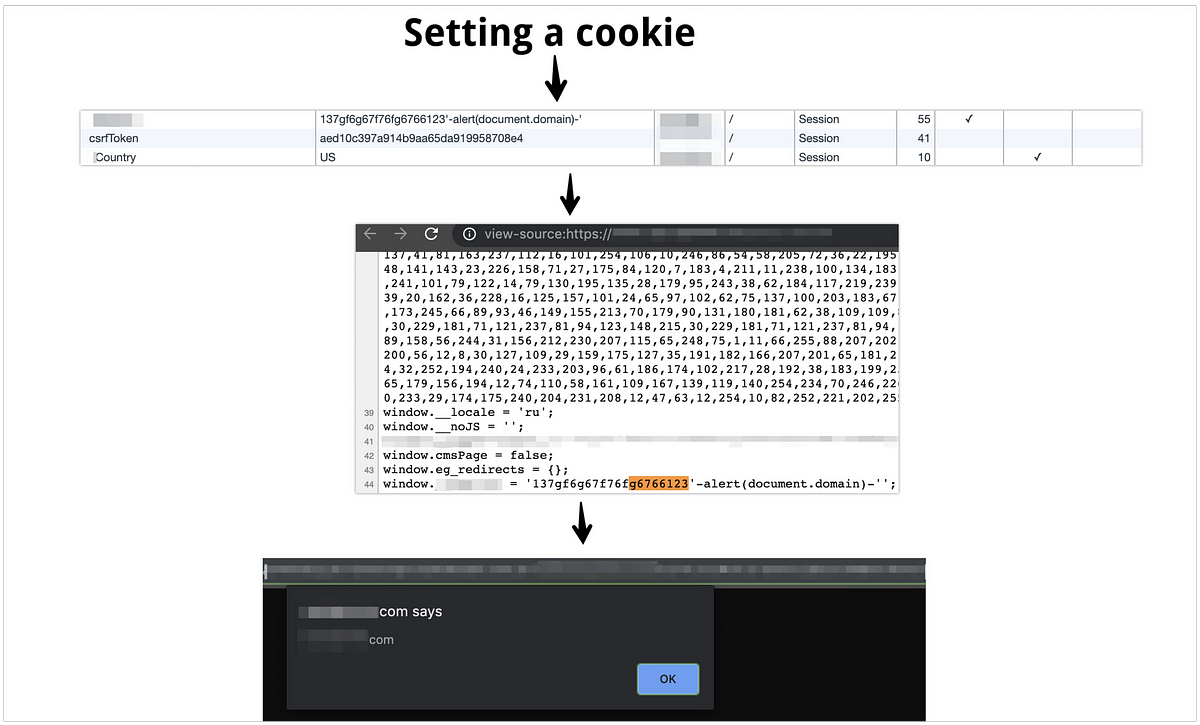
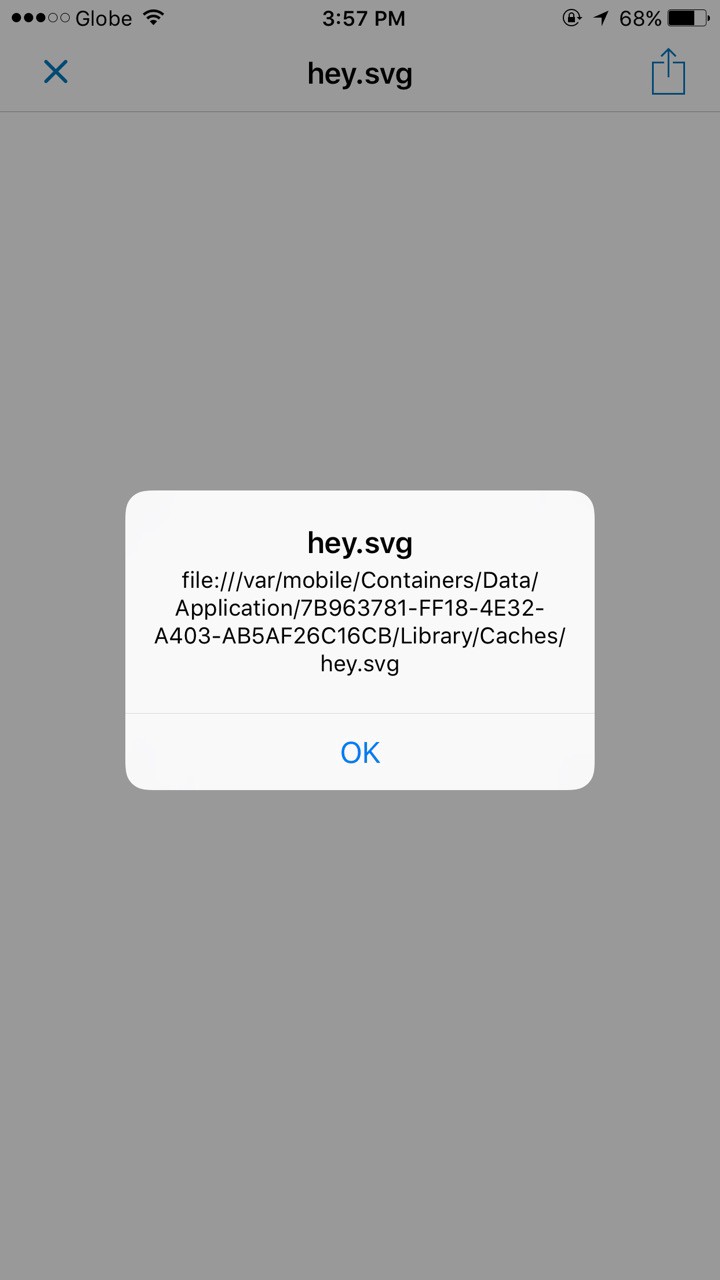
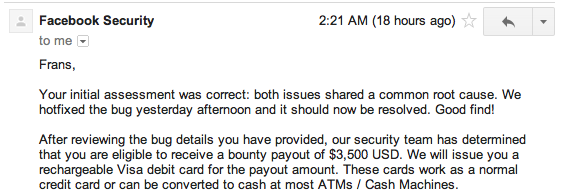
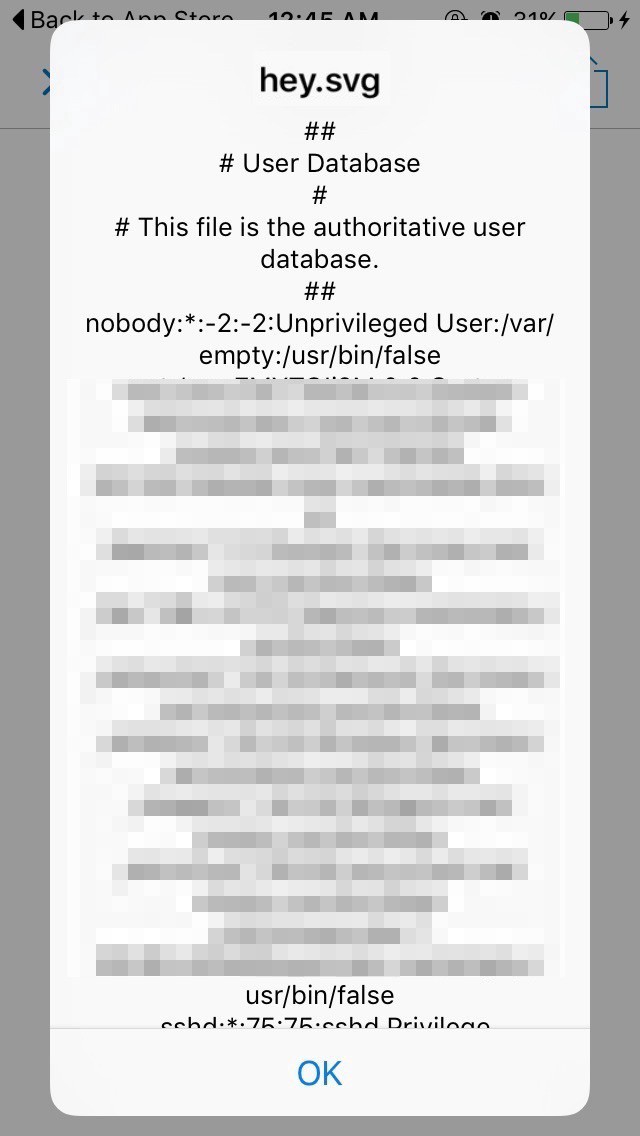
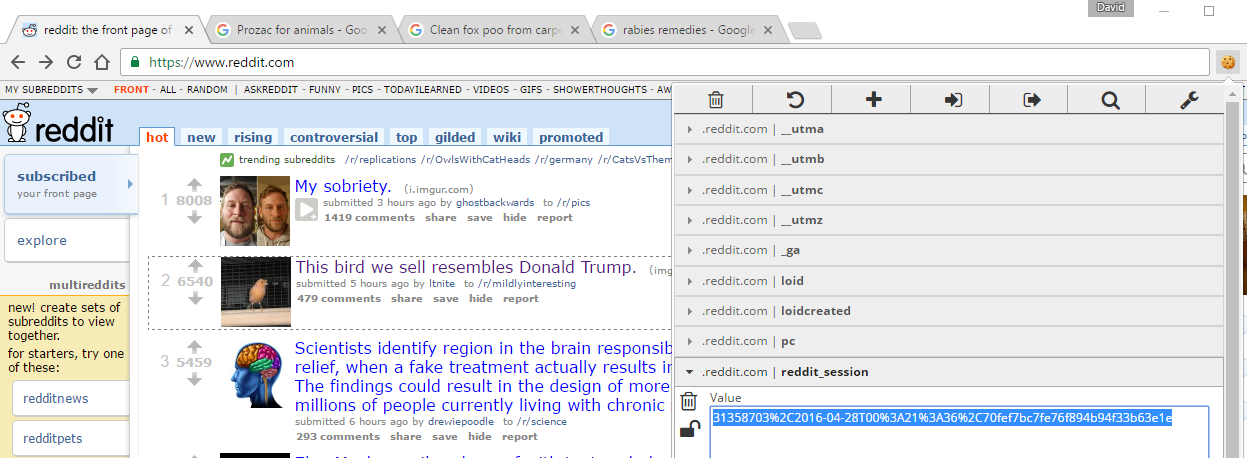
Noon Com Cross Site Scripting Vulnerability Open Bug Bounty

Dim will save your tags loadouts and settings to the dim servers and sync them between different versions of dim.
Noon com cross site scripting vulnerability open bug bounty. All contents of this site constitute the property of isc inc. Pi system is the system of record for operational data. We would like to show you a description here but the site won t allow us. Isc cissp sscp ccsp cap csslp hcispp cissp issap cissp issep cissp issmp and cbk are registered certification marks of isc inc.
Assigned by cve numbering authorities cnas from around the world use of cve entries ensures confidence among parties when used to discuss or share information about a unique. My name is kreekcraft and i livestream roblox and other games everyday. I mainly make videos on roblox piggy theories and new updates but i also make v. For over 40 years our software has enabled industry to collect standardize contextualize and federate large volumes of industrial operational data.
Common vulnerabilities and exposures cve is a list of entries each containing an identification number a description and at least one public reference for publicly known cybersecurity vulnerabilities. Our cases give great odds on the best items from the sought after dragon lore medusa and much much more. And may not be copied reproduced or distributed without prior written permission. Enjoy the videos and music you love upload original content and share it all with friends family and the world on youtube.
Our mission is to promote sustained non inflationary economic growth and a sound and progressive financial centre.